ISO 27001 Certification in Jordan
ISO 27001 Certification In Jordan
ISO Certification In Jordan, Certivatic is specialized in providing ISO Certification and Consultation in Jordan. We provide the best ISO Consultant services in Amman, Russeifa, Zarqa, Irbid, and other major cities in Jordan with the service of consultation, implementation, documentation, training, auditing, and registration. We do provide CE mark Certification, HALAL Certification around the world at an affordable cost.
The ISO 27001 certification in Jordan applies to many parts of an organization. There are many aspects of ISO 27001 audit services in Jordan that are aimed at maintaining the security information that is only necessary to handle by the management to protect the organization from many external and internal factors that affect the organization.
What is ISO 27001 Certification in Jordan?
ISO 27001 Certification in Jordan is designed to function as a framework for an organization’s information security management system (ISMS). An ISO 27001 is a structure of policies and processes that contains all legal, physical, and technical controls involved in an organization’s information risk management processes.
It allows you to prove to your customers, interested parties, and shareholders that you are managing the information security of your information.

Get Free Consultation
Downloads
ISO Certification In Jordan
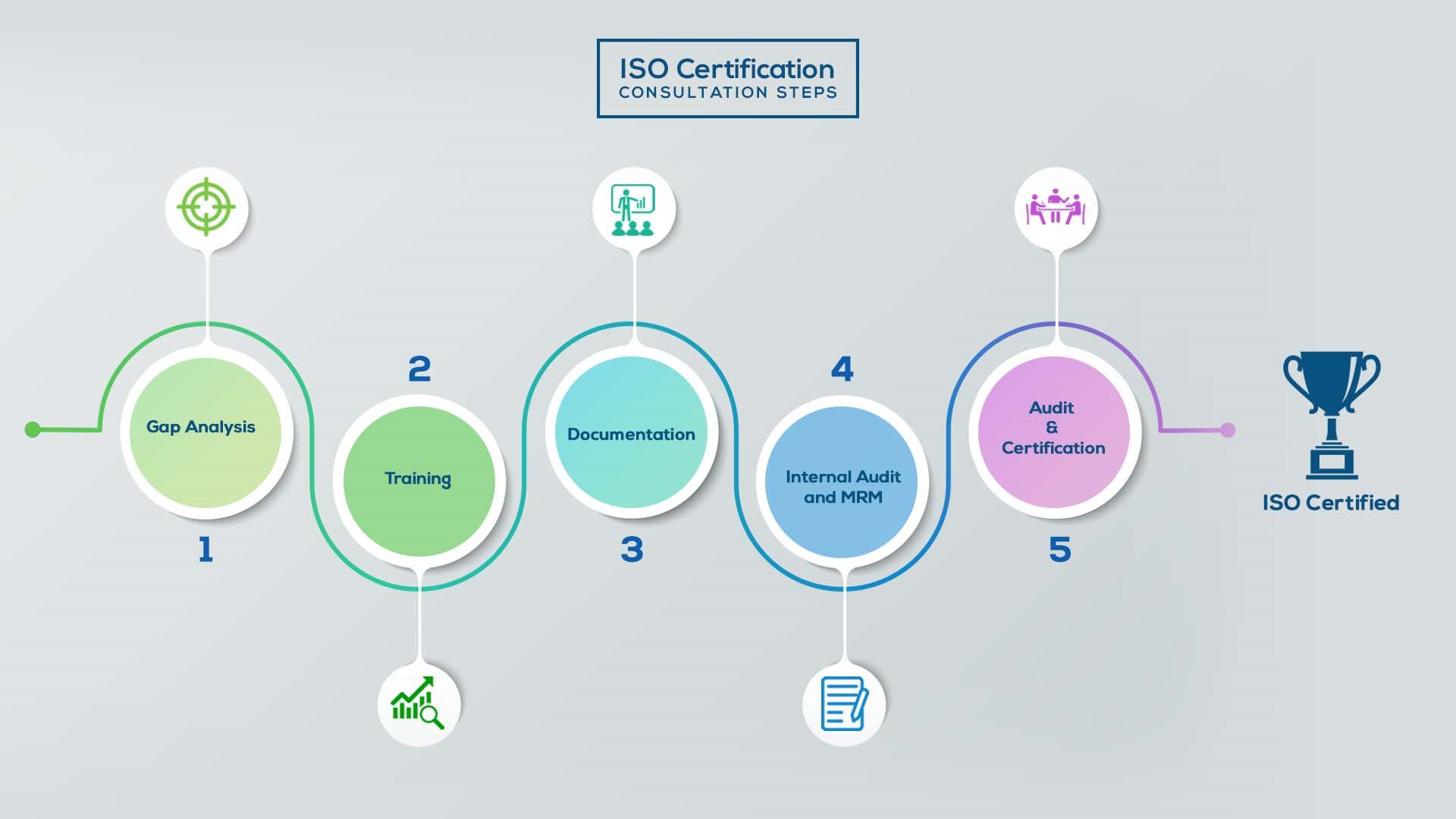
Our method/steps are easy, unique, time-bound, and result-oriented.
Gap Analysis:
- Interacting and detailed study of current work flows in different departments, operating procedures, documentation and practices.
- Identifying any shortcomings of your organization against the requirements of ISO.
- Generating a Gap report and planning for implementation
Training:
- Creating awareness about ISO standard and its importance.
- A formal training session/s.
- It includes training on internal auditing, documentation training, mock audit and trainings to conduct management review meeting.
Documentation:
- Documentation is the manifestation for your entire organizations process, procedure and results.
- End-to-End support on preparing documentation as per ISO requirements.
Internal Audit & MRM:
- Internal Audit (IA) as a tool, it is a cross departmental audit to ensure zero loophole in the system of your organization.
- MRM: Management review meeting (MRM) helps top management to guide and ensure the whole organization is up to the mark as per the standard requirements.
Final Audit and Certification:
- Certivatic – Your certification is our responsibility!
- With our 100% track record of success, we make sure Certification is achieved successfully.


All about ISO 27001 Certification in Jordan
Implement Access Control Firstly, what are permissions and what an end-user is allowed to do on the system depend upon the account used and what that account has been configured to allow the user to do. Most operating systems allow very granular control as to what a particular account is allowed to do. Configure accounts to allow users the access rights necessary to perform their job but no more. This if you recall is the principle of least privilege access rights consists of an account’s ability to access files and directories. If access is granted to a file is the account allowed to change or only read it. If access is granted to a directory is the account, only allowed to read the contents of that directory or are they allowed to create new files in the directory, etc. creating these rights on a Linux or Windows, Operating System is a very basic admin function and for ease of administration.
Assign rights to groups of accounts, rather than to individual accounts. You should create groups of employees with similar job functions and then assign specific rights to the group. For example, all junior accountants will get a specific set of permissions. While all senior accountants will get a different and probably more permissive set of permissions. All admin assistants will get a specific set of permissions applicable to their job duties, etc. remote access permissions need to be considered carefully. Prior to granting such permission, the reason why you would hesitate to grant the same permissions from a remote location as you would from your company location is that the security of the remote site is unknown. If you plan to allow end-user access from a potentially insecure low location to data on your network, you should use a VPN; a VPN provides secure communication over an insecure public network. So what’s going to happen is the data that goes back and forth will be encrypted and there are two types of VPN site to site VPN and client-based VPN.
So what is a client-based VPN? Here, a piece of software is installed on the end user’s laptop this allows the remote user to establish a VPN from his laptop to the security appliance that sits on your home network. The important thing to realize is that the VPN allows all data between the laptop and the remote network to be tunneled and therefore encrypted. So you don’t really care if the connection is secure or not. Because even if the data could be sniffed by a black hat it would not be able to decrypt the encrypted data. Also, make sure that the VPN is enforced meaning that the end-user is unable to connect to the home office unless the data is perfect is protected by the VPN.
ISO 27001 certification in Jordan spotlights on Information security the executive’s framework in the association. In different terms data is likewise called a resource, and can be utilized as an influence against any association where the proviso can be found. The security level of data security in each area of the Limited admittance and divider against certain data must be constructed with ISO 27001 Certification in Jordan.
For More Information Visit: ISO 27001 Certification in Jordan


