ISO 27001 Certification In Malaysia
ISO 27001 Certification in Malaysia
ISO 27001 Certification In Malaysia, Certivatic is specialized in providing ISO 27001 Certification and Consultation in Malaysia. We provide the best ISO Consultant services in Kuala Lumpur, George Town, Malacca, Johor Bahru, and other major cities in Malaysia with the service of consultation, implementation, documentation, training, auditing, and registration. We do provide CE mark Certification, HALAL Certification around the world at an affordable cost.
ISO 27001– Information Security Management System
ISO 27001 certification in Malaysia is an international standard which sets out requirement for Information Security Management System. ISMS enhancements a reputation and builds trust in an organisation. By implementing ISO 27001 standard it allows organizations of any kind to manage the security of assets such as business information, staff information or information assigned by third parties. ISO 27001 certification in Malaysia can be implemented by any organization regardless of its size, type or nature of business.
Working toward an ISO 27001 Certification in Malaysia is certainly not a simple task for any company dimension. However, it seems to get increasingly more complicated the larger you are. Like any safety and security protocol, it needs to be done deliberately and extensively to obtain holistic protection and Certification. It means no faster ways, workarounds, or reducing any edges.

Get Free Consultation
Downloads
ISO Certification In Malaysia
- ISO 9001 Certification In Malaysia
- ISO 14001 Certification In Malaysia
- ISO 22000 Certification In Malaysia
- ISO 27001 Certification in Malaysia
- ISO 45001 Certification in Malaysia
- ISO 13485 Certification in Malaysia
- ISO 17025 Certification in Malaysia
- CE Mark Certification in Malaysia
- Halal Certification in Malaysia
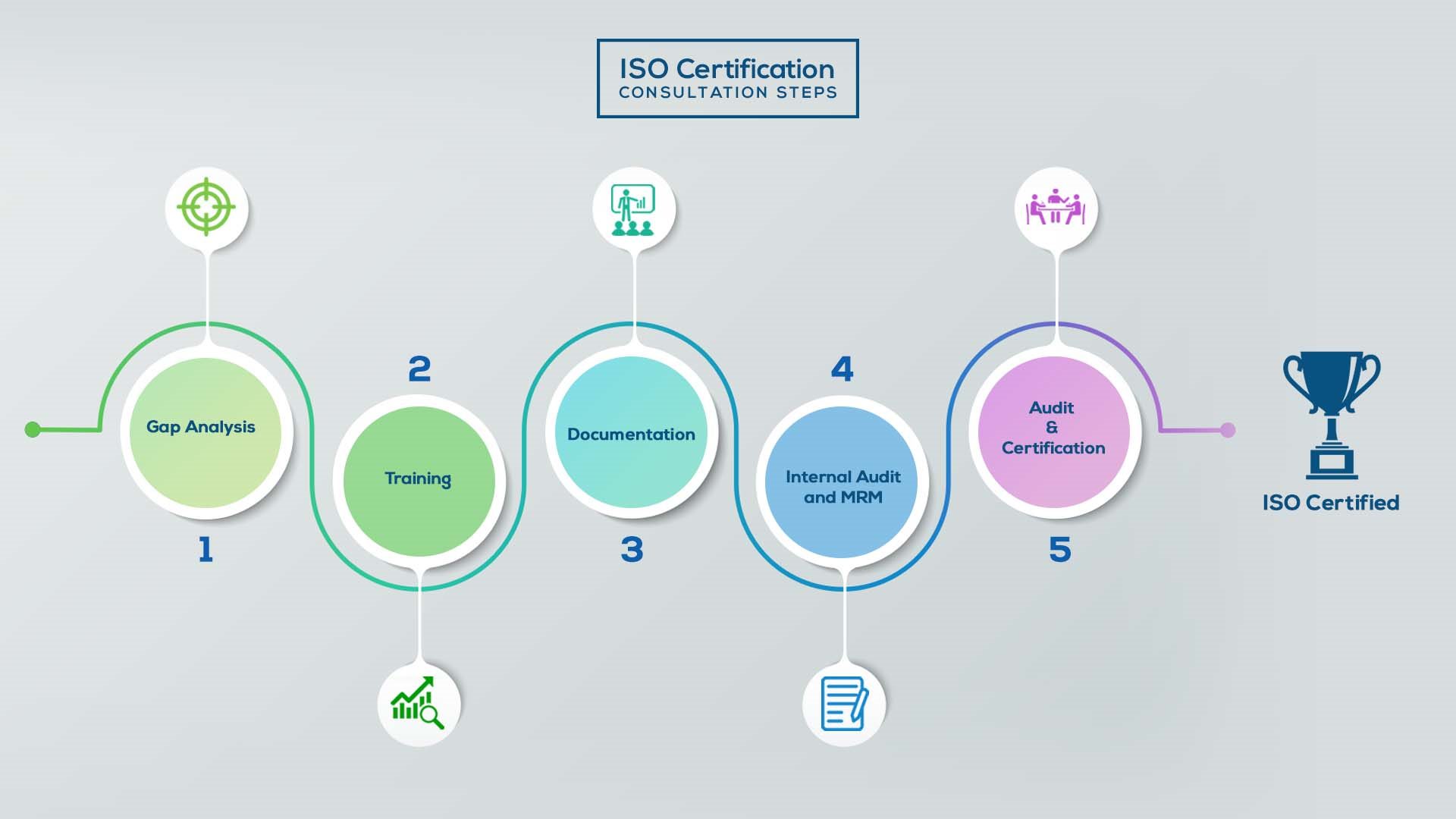
Our method/steps are easy, unique, time-bound, and result-oriented.
Gap Analysis:
- Interacting and detailed study of current work flows in different departments, operating procedures, documentation and practices.
- Identifying any shortcomings of your organization against the requirements of ISO.
- Generating a Gap report and planning for implementation
Training:
- Creating awareness about ISO standard and its importance.
- A formal training session/s.
- It includes training on internal auditing, documentation training, mock audit and trainings to conduct management review meeting.
Documentation:
- Documentation is the manifestation for your entire organizations process, procedure and results.
- End-to-End support on preparing documentation as per ISO requirements.
Internal Audit & MRM:
- Internal Audit (IA) as a tool, it is a cross departmental audit to ensure zero loophole in the system of your organization.
- MRM: Management review meeting (MRM) helps top management to guide and ensure the whole organization is up to the mark as per the standard requirements.
Final Audit and Certification:
- Certivatic – Your certification is our responsibility!
- With our 100% track record of success, we make sure Certification is achieved successfully.
Benefits of being ISO 27001 certified are:
- Improves customer confidence and winning more business
- Improved reliability and security of systems and data
- Aware employees and contractors of the risks and incident reporting.
- Protect financial losses by reducing data breaches and incidents.
- Comply with legal, contractual and regulatory requirements
- Increase in sales and customer satisfaction
- Improved company image and reputation
The key concepts of Information Security Management System – ISO 27001?
The key concepts of Information Security Management System are as below
- Confidentiality is information is accessible only to those who are authorized to view it. That means a person in a hierarchical way, he is from the level one category, assume he is from the level one category, so he will be having some accesses only that is only read accesses. So the level two people will be having read plus write access on some documents or some drives the same way, the manager will be having read and write access. So, based on that, the confidentiality of the information is protected and the data is safe.
- Integrity information especially when being communicated. It is protected against unauthorized modifications that means when you are sending an emails, assume you’re sending an email from your project or your company’s email ID to the customer. So it should be protected because in the data transfer there might be hacked hackers or any other person who can view it. So, it should be pin protected or password protected.
- Availability the information is in vulnerable to attacks or is to be recovered in a secured way. That is, it should be available when it should be that means only the authorized people should be accessing it, as well as it should be the availability of the data should be there, so that the data should not be missed.
- Non-repudiation sendoff information cannot deny that information has not been sent by him so that means that it should be authorized as well as it should be available and also it should be confirmed. It got from the correct domain or it got from the correct person.
- Information security policy an organization which ensures the compliance of information security objectives and guidelines that means based on the objectives and guidelines the organization develops a policy and uses it to their organization or a project by following this information security policy.
- Security analysis and controls to analyze the threats to organizations data and to eliminate the same. So that means to protect the data as well as information, based on this security plans to provide security controls at various levels so that to reduce the impact of security breaches. So for security breaches also, we have some checkpoints so that by this checkpoints we can eliminate those breaches and provide security.
ISO 27001 certification in Malaysia is the most powerful ISO standard when it comes to building the walls across each
level of the organisation. Some of the data will be reserved for some people from the top
management system and to apply this procedure the kind of software and the Firewalls must be
implemented in the organisation from ISO 27001 Certification in Malaysia with Certivatic.
For any further information visit ISO 27001 certification in Malaysia


